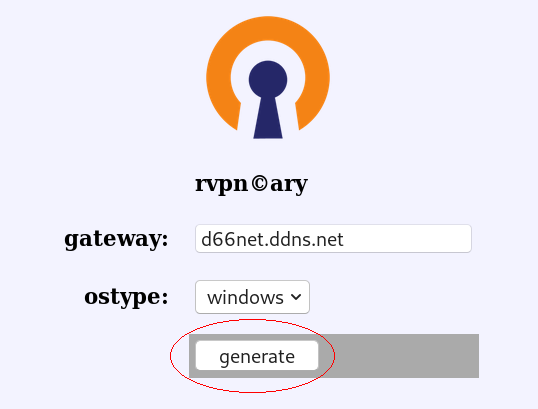
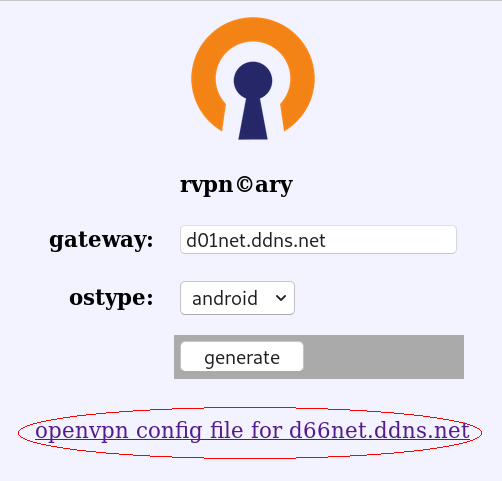
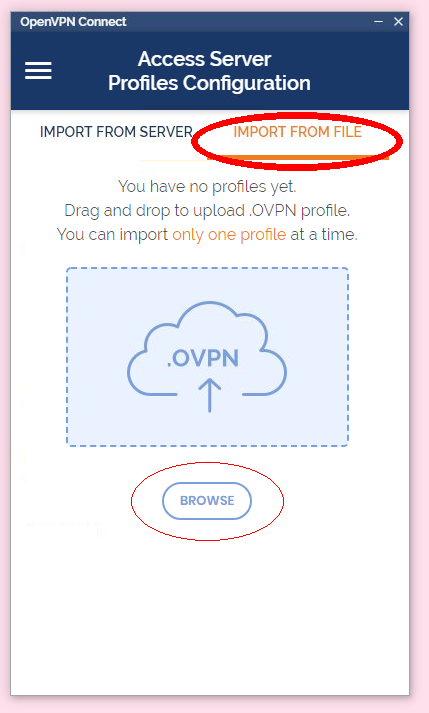
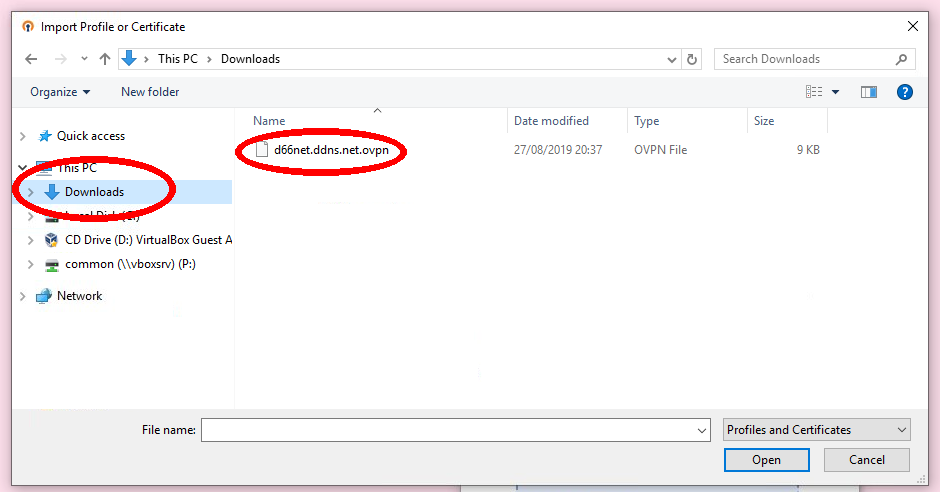
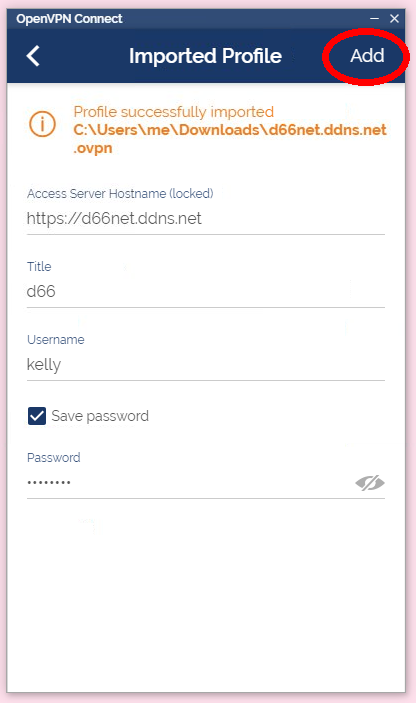
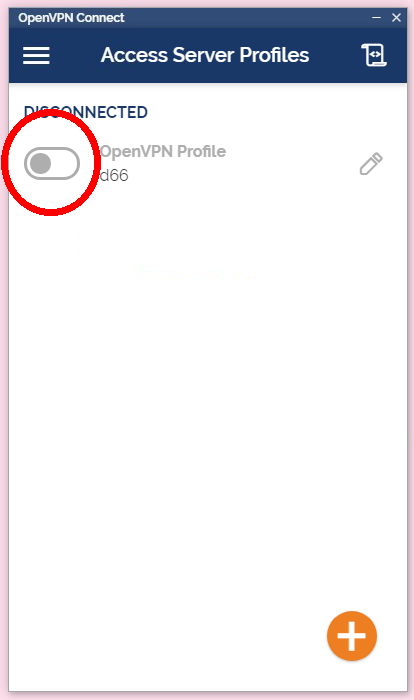
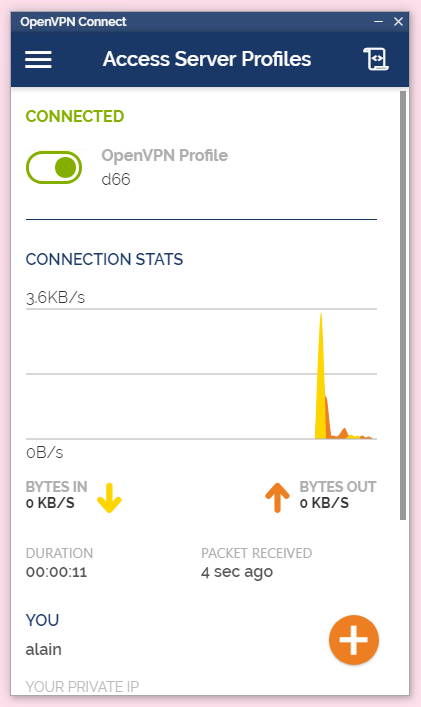
1. download ovpn file
2. linux
dnf install NetworkManager-openvpn-gnomewget -N -nv http://users.telenet.be/d09/sharel/zip/d01-1.0.ovpn -P ~/Downloads/
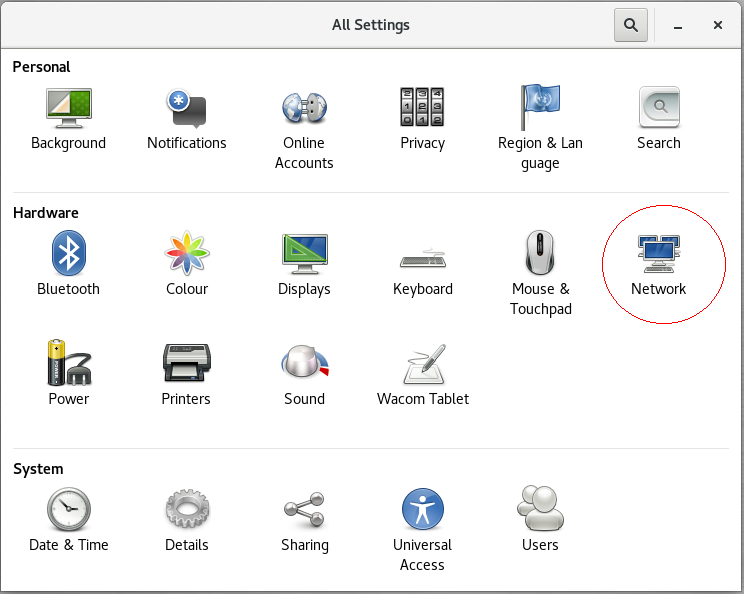
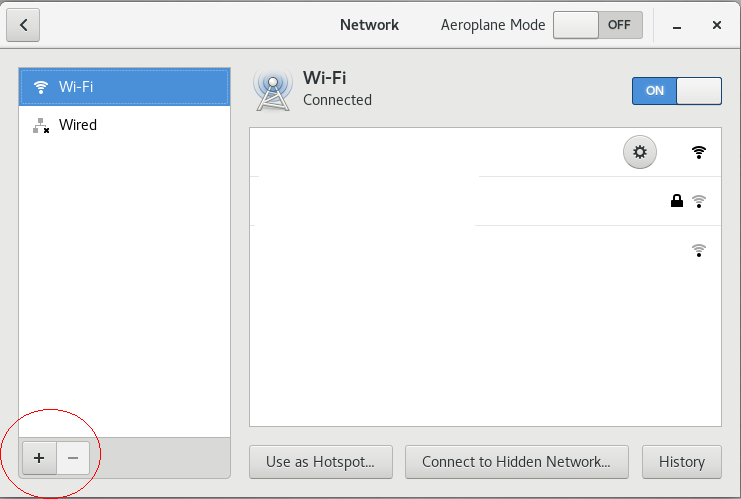
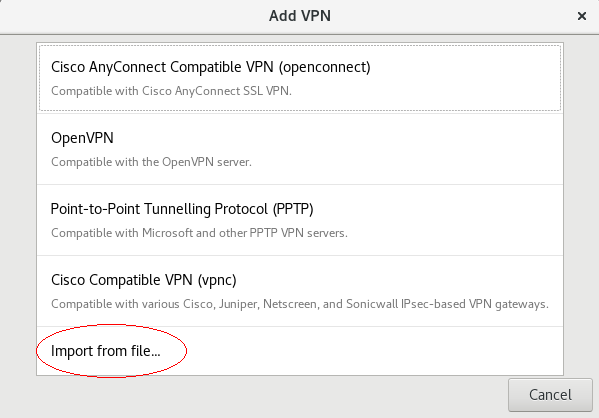
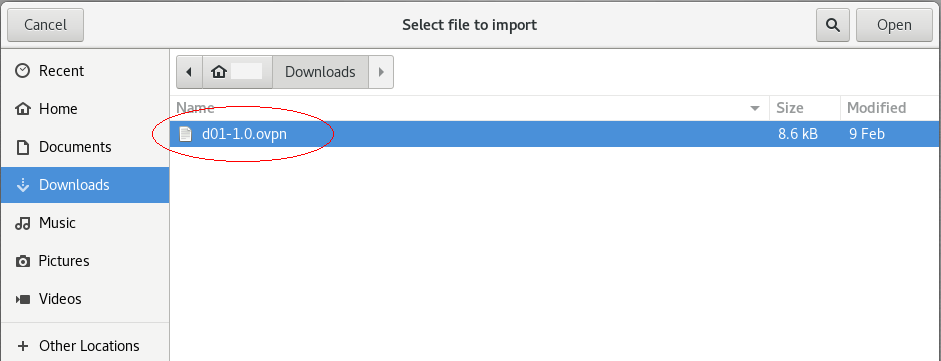
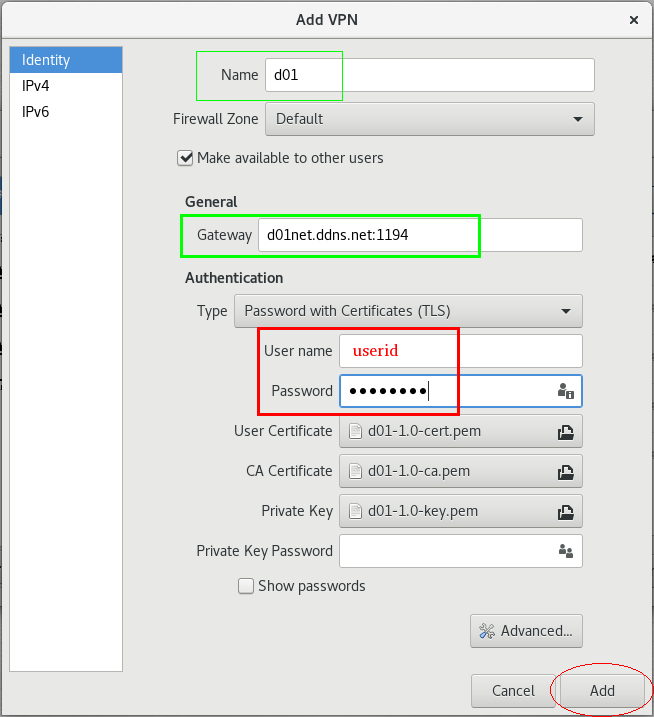
4. macos
7. logging on server
Tue Mar 27 23:18:38 2019 TCP connection established with [AF_INET]94.225.180.106:49707
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 TLS: Initial packet from [AF_INET]94.225.180.106:49707, sid=0784e6af f9d37bbd
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 VERIFY OK: depth=1, C=BE, ST=BE, L=BE, O=BE, OU=d01, CN=BE CA, name=cid, emailAddress=admin@d01.net
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 VERIFY OK: depth=0, C=BE, ST=BE, L=BE, O=BE, OU=d01, CN=client, name=cid, emailAddress=admin@d01.net
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_VER=3.git::1ab9727b
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_PLAT=win
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_NCP=2
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_TCPNL=1
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_PROTO=2
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_LZO_STUB=1
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_COMP_STUB=1
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_COMP_STUBv2=1
Tue Mar 27 23:18:38 2019 94.225.180.106:49707 peer info: IV_BS64DL=1
Tue Mar 27 23:18:39 2019 94.225.180.106:49707 PLUGIN_CALL: POST /usr/lib/openvpn/plugins/openvpn-plugin-auth-pam.so/PLUGIN_AUTH_USER_PASS_VERIFY status=0
Tue Mar 27 23:18:39 2019 94.225.180.106:49707 TLS: Username/Password authentication succeeded for username 'kelly' [CN SET]
Tue Mar 27 23:18:39 2019 94.225.180.106:49707 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Tue Mar 27 23:18:39 2019 94.225.180.106:49707 [kelly] Peer Connection Initiated with [AF_INET]94.225.180.106:49707
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 MULTI_sva: pool returned IPv4=10.99.0.6, IPv6=(Not enabled)
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 MULTI: Learn: 10.99.0.6 -> kelly/94.225.180.106:49707
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 MULTI: primary virtual IP for kelly/94.225.180.106:49707: 10.99.0.6
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 PUSH: Received control message: 'PUSH_REQUEST'
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 SENT CONTROL [kelly]: 'PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 10.66.1.2,dhcp-option DOMAIN d66.net,route 10.99.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.99.0.6 10.99.0.5,peer-id 0,cipher AES-256-GCM' (status=1)
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 Data Channel: using negotiated cipher 'AES-256-GCM'
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key
Tue Mar 27 23:18:39 2019 kelly/94.225.180.106:49707 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key